Software as a service (SaaS) is a fast-growing market segment that is projected to grow to USD 1.1 billion by 2032. As more businesses rely on cloud solutions, they seek technology to help them scale. The growing number of customers leads to a crucial question: how can you trust us with your most valuable data – your recipes and nutritional information?
That’s where The System and Organization Controls (SOC) comes in.
This article will simplify the complicated world of SOC frameworks so you can understand the basics without needing to be an expert. It’ll also dive into why they’re an essential requirement for SaaS companies (including us!) that want to put their customers’ trust first.
To take a deeper dive into our platform and enterprise features, book a demo with an expert.
Update: December 2025 We are proud to announce that Food Label Maker has officially achieved SOC 2 Type II Compliance. This milestone reflects our ongoing commitment to the highest standards of data security and privacy for our customers.
Overview of SOC Reports
For us at Food Label Maker, our commitment to your data security is at the core of our operations. That’s why we’re dedicated to upholding The System and Organization Controls (SOC) framework.
These reports are developed by The American Institute of Certified Public Accountants (AICPA) designed to make sure organizations handle and store customer data securely. These reports are created in a way to help build trust with a range of stakeholders, as these reports set controls in place for enterprises to protect financial data and sensitive client information. Nowadays, with technology being our go-to in our daily lives, it’s important to have frameworks in place that protect the data shared and exchanged. Any mishandling of data can leave enterprises vulnerable to attacks, such as data theft, extortion and malware installation.
SOC reports are essentially audits that are carried out by an independent Certified Public Accountant (CPA) firm to ensure companies are adhering to the standards set by the AICPA. This process is carried out by a CPA firm because they have deep experience implementing professional standards and establishing industry oversight.
SOC Certification or Attestation?
You’ve probably Googled and seen a lot of “SOC 2 Certified” or “SOC 2 Certification”, which might have left you a little confused because there isn’t an actual SOC certification that comes out of this process.
Simply put, a SOC audit doesn’t result in a company being “certified.” Instead, it results in a report that attests, meaning it gives proof or a testimony, to whether or not the company’s controls are designed and operating effectively over a specified period. The AICPA oversees the SOC framework, and any licensed CPA can then perform the audit, but the AICPA does not issue a certification.
The word certification is used when there is a pass/fail assessment according to a specific standard, which results in an official certificate being granted. An attestation, in this case, is a formal report from a third-party auditor that provides their professional opinion based on a set of criteria.
Usually, the term ‘SOC Certification’ is used by companies that want to showcase this win and communicate it loud and proud, which is great, but make sure to use the correct terminology!
There are 3 main types of SOC reports, each serving its own purpose. While there are 3 types of SOC reports, the main ones that are always talked about are SOC 1 and SOC 2.
What is SOC 1 vs SOC 2?
At Food Label Maker, SOC (pronounced “sock”) is a framework we follow and implement to demonstrate our security commitments. It’s important to note that none of these frameworks are mandatory at all meaning businesses can voluntarily choose whether or not they want to follow and implement the standards.
SOC 1 Definition
SOC 1 is an audit that focuses on financial reporting practices. These services include:
- IT infrastructure
- Payroll
- Recordkeepers
- Investment advisors
While a SOC 1 audit is a critical framework for service organizations that impact a client’s financial reporting, it is not a focus for our business. We are dedicated to SOC 2 as it directly impacts your data.
If you’d like to read up more on SOC 1 and its details, explore Linford & Company LLP’s piece: What is a SOC 1 Report? Expert Advice for Audit Compliance.
SOC 2 Definition
Our main commitment is to SOC 2, as it directly addresses the security and confidentiality of your most valuable data – your recipes and nutritional information.
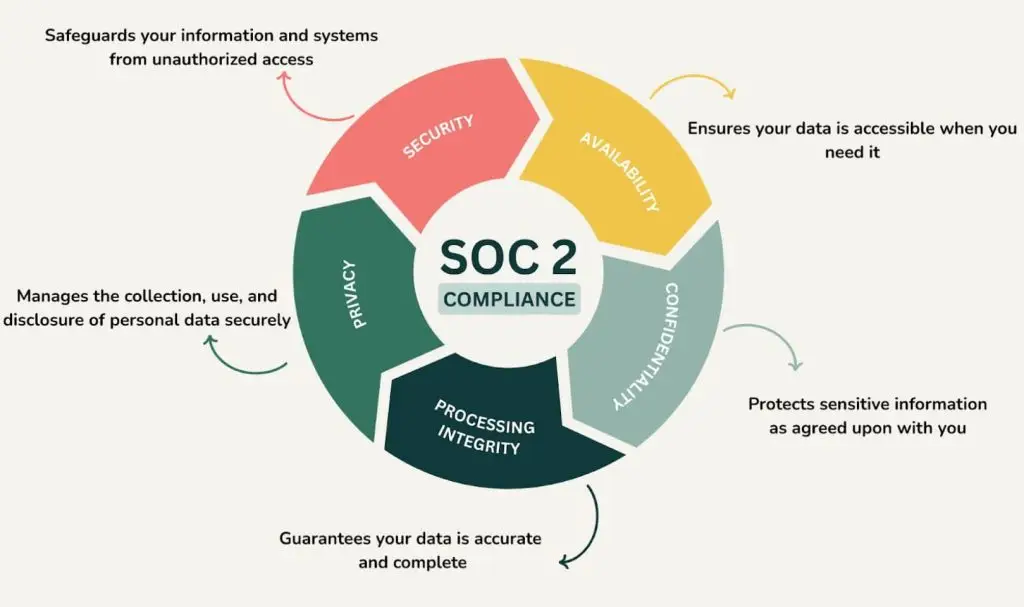
SOC 2, by definition, is a voluntary cybersecurity compliance framework that specifies how organizations should manage customer data based on the 5 Trust Services Criteria (TSC):
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 has been specifically designed for companies that store sensitive client data in the cloud. This basically covers most SaaS companies and cloud vendors. As we are a SaaS company, this framework is specifically tailored to our needs and our commitment to you.
SOC 3 is a report with the same controls as SOC 2, but is instead a high-level summary revealed to, and written for, the general public. For example, an organization that achieves SOC 2 compliance may also create a SOC 3 report to let the general audience know that it takes data security and privacy seriously.
Understanding the 5 Trust Services Principles of SOC 2
To ensure your data is always protected on our platform, we’re committed to the five SOC 2 Trust Principles. They are the core of our security posture and provide the following protections for your recipes and business data:
SOC 2 Type 1 vs Type 2
To provide you with a full picture, it’s helpful to understand the difference between the two types of SOC 2 reports: Type I and Type II. This might sound complicated but below is a simplified table to help explain the difference between the two.
| Feature | SOC 2 Type 1 | SOC 2 Type 2 |
|---|---|---|
| Audit Period | A single point in time | Over a period of time (typically 3-12 months) |
| What it Verifies | The design of your security controls, confirming policies are suitable. | The operational effectiveness of your controls, proving policies are consistently followed. |
| Level of Assurance | Lower assurance, showing what’s in place at one moment. | Higher assurance, showing controls work continuously. |
| Typical Use Case | Used by startups for a quick report to close a deal or for initial compliance. | Required by large enterprises needing a proven track record. |
| Time to Complete | Shorter (weeks to a few months). | Longer (several months to a year). |
| Cost | Less expensive due to the shorter audit period. | More expensive due to extensive evidence collection. |
See How FoodLabelMaker Can Help You
How do you get SOC 2?
And now we can tackle the question that’s probably on your mind: How does a company become SOC 2 compliant?
For us, it’s less about checking off boxes and going through a one-and-done process. It’s about actively working to improve our security posture and demonstrating that we can securely manage data and protect client privacy. The AICPA designed the SOC 2 framework in a way that explains what the main principles are and allows each enterprise to choose the criteria that work with each business’s clients’ needs.
Here’s Sprinto’s 9-step SOC 2 checklist to help you see some main points we’re following towards becoming SOC 2 compliant:
- Choose your objectives
- Identify the type of SOC 2 report you need
- Define your SOC 2 scope
- Conduct an internal risk assessment
- Perform gap analysis and remediation
- Implement relevant controls and test them
- Undergo readiness assessment
- Conduct the SOC 2 audit
- Establish continuous monitoring practices
And for a more detailed breakdown, read through Sprinto’s SOC 2 Requirements: Essential Guidelines for Compliance.
Why is SOC 2 Important?
It may seem like a lot of work to put towards a process that’s not mandatory by law, but the benefits of being compliant with SOC 2 make it all worth it.
For those familiar with the food industry, like us, it can be helpful to think of the SOC 2 Framework similar to HACCP or ISO 22000.
HACCP is defined by the FDA as: A food safety management system that controls biological, chemical, and physical hazards throughout the food production process, from raw materials to the final product.
ISO 22000 is defined as: an international standard that specifies the requirements for a food safety management system (FSMS).
Both of these systems are put in place for food management organizations to ensure the safety and quality of food products. The SOC 2 Framework follows the same purpose but for data instead.
Some key benefits of being SOC 2 Compliant include:
- Improve the overall security outlook
- Help customers feel confident in sharing their data with us
- Increase brand reputation as a security-conscious company
- Avoid data breaches and the damage (financially and reputation-wise) that come with them
Just as HACCP and ISO 22000 are the gold standard for food safety, SOC 2 is the gold standard for data security, providing a strong framework that protects customer information and builds trust with Food Label Maker.
Conclusion: Where We Are | Food Label Maker
We’re thrilled to announce that as of December 2025, Food Label Maker has officially achieved SOC 2 Type II Compliance – a testament to our unwavering commitment to protecting our clients’ data.
Over the years, we’ve emerged as an industry leader in data security, and we take pride in the measures we’ve implemented. We uphold a set of standards to ensure that your data is stored effectively and safely on our platform for structured everyday use. This milestone achievement is yet another step we’ve taken towards implementing the gold standard of cybersecurity compliance framework that ensures your data is stored securely. Working towards SOC 2 Compliance is yet another step we’re taking towards implementing a rock-solid cybersecurity compliance framework that ensures your data is stored securely.
Why Our SOC 2 Achievement Matters As of December 2025, our formal audit is complete. For our users, this means:
- Verified Protection: An independent auditor has verified that our internal controls for managing and securing data are airtight.
- Enterprise Readiness: We are now fully equipped to meet the rigorous vendor requirements of global food manufacturers.
Continuous Improvement: SOC 2 isn’t a “one and done” certificate; it requires annual audits, ensuring we never let our guard down.
We are committed to taking these and future steps to keep your information safe, because your data’s security is our top priority.
Thinking about a solution for your whole team? Book a demo to learn more.
Frequently Asked Questions About SOC 2 Compliance
Where is SOC 2 most commonly used?
SOC 2 is a very common practice in North America, mainly in the U.S. It’s very widely known that any company wishing to do business with organizations in the U.S. must obtain SOC 2 Attestation in order to be considered.
With its growing popularity, SOC 2 is making its way to Europe with more organizations recognizing its benefits.
Find the perfect plan for your business by booking a demo or creating a free label to try it out.
Are SOC reports mandatory?
No, SOC reports are not required by law to be carried out. They are completely voluntary and organizations will not be penalized for not being compliant to any SOC type. However, it’s important to note that while they aren’t mandatory, they are really important in building customer trust and confidence. So, being compliant will definitely go a long way.
Ready to get started? Book a demo or create a free label
What is the difference between ISO 27001 and SOC 2?
There are many key differences between ISO 27001 and SOC 2 but the main difference is in the scope.
ISO 27001 is a global standard that provides companies with the correct guidance to improve their Information Security Management System (ISMS). On the other hand, SOC 2 is a set of audit reports carried out by an independent CPA firm that attests to how well a company’s security controls are working over a specific period of time. ISO 27001 can be seen as more definitive across all sectors and organizations whilst SOC 2 is more flexible depending on the company’s needs and the industry’s standards.
Both standards follow similar principles so if you choose to attain one, you’re well on your way to obtaining the other. Several key factors come into play such as cost and bandwidth within the company to take on an extra standard of protocols.
Start by booking a demo or creating a free label.


